Fortifying the Factory Floor: Cybersecurity for the Smart Manufacturing Industry
September 10, 2025
Introduction
Smart manufacturing, IIoT devices, and digital transformation are proving to be the primary contributors of rapid and beneficial changes in the manufacturing landscape. Manufacturers can boost operational resilience, cut expenses, and optimize efficiency owing to this technological surge. But increased connectedness also means greater vulnerability. The scope of attack for malevolent cyber activity keeps expanding as production systems depend more and more on clever technology and connected devices.
This blog is intended for plant managers, chief information security officers (CISOs), OT/IT integrators, and stakeholders in the manufacturing industry who are negotiating the ever-complex landscape of OT security. Whether you supervise manufacturing operations on the production line, manage important infrastructure, or oversee the cybersecurity team, it is not only essential but also critical to understand how to protect your OT systems.
This blog will help you learn about the specific cyberthreats that target the manufacturing industry, how contemporary technologies like multifactor authentication, network security, and vulnerability management reduce cyber risks, and practical techniques for safeguarding industrial networks and OT systems from data loss and failures.
Furthermore, it will enable you to make better business decisions, shield your intellectual property, and ensure the investments you make in Industrial Internet of Things (IIoT) technology are safe, legal, and productive.
The Rise of Smart Manufacturing and Cyber Exposure
Cloud computing, data collection, and communication protocols are being progressively incorporated into traditional control systems as businesses embrace intelligent production and industrial IoT technologies. From real-time performance metrics to predictive maintenance, these advancements support everything. However, each advancement broadens the network of linked devices, boosting the number of potential ports of entry for cybercriminals.
PLCs and dispersed control systems, which were formerly air-gapped, are now integrated into complicated OT networks. Unfortunately, these OT settings are susceptible to hackers since they were not created with data safety in mind. Given that these environments frequently require physical procedures, unlike traditional IT systems, any intrusion raises concerns regarding both data security and physical safety.
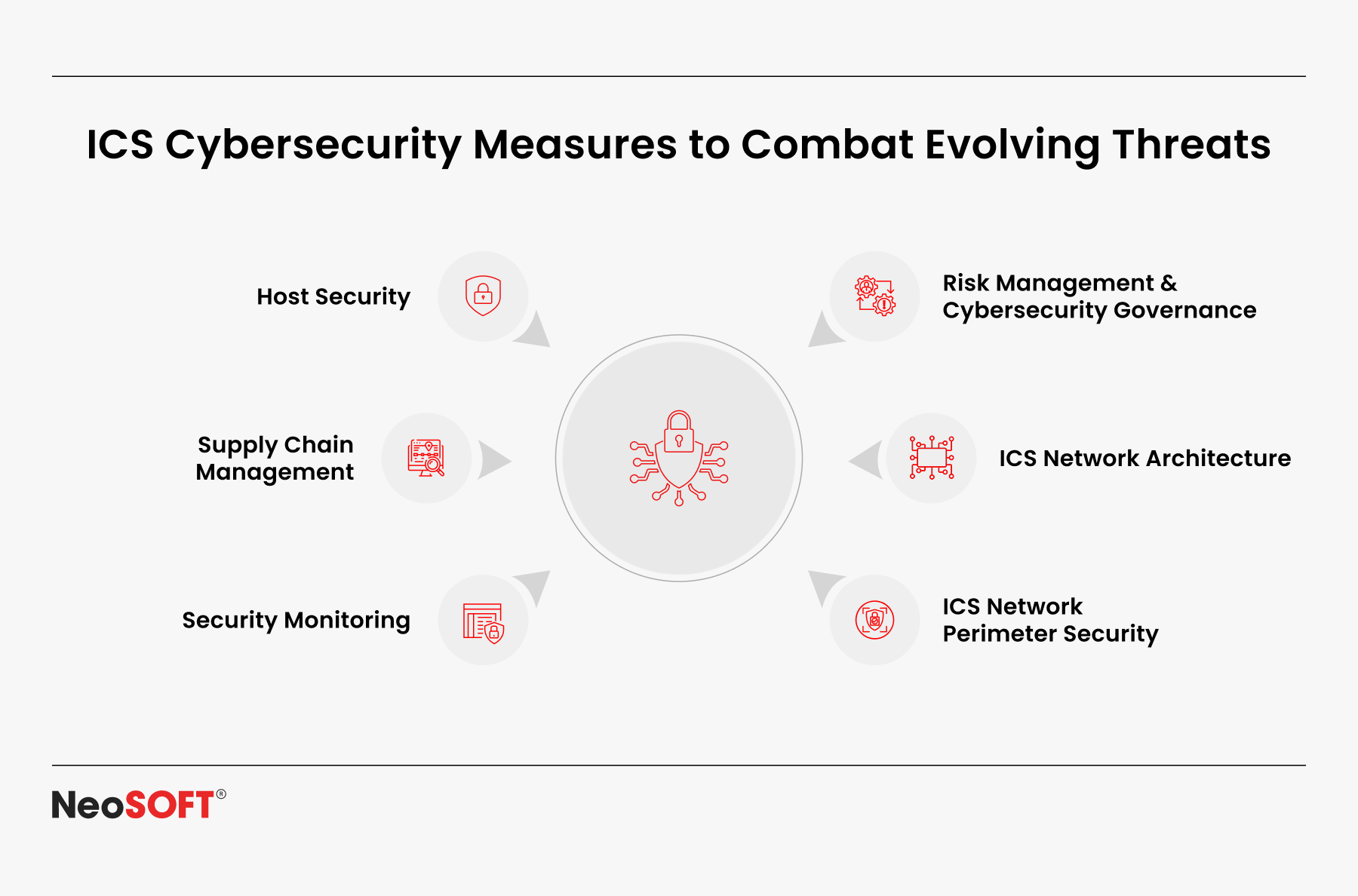
Top Cybersecurity Threats Facing Industrial Control Systems
The convergence of information technology and operational technology (OT) creates significant security vulnerabilities. Key threats include:
- Remote access misuse by third-party vendors, maintenance crews, or compromised credentials.
- Malware affects industrial management platforms, including supervisory control tools.
- Attacks on production lines that disrupt uptime and compromise operational efficiency.
- Supply chain assaults using hacked hardware updates or software from OT vendors.
- IP theft and IIoT data theft, including specifications for designs and confidential procedures.
- Campaigns of ransomware including LockerGoga, Ekans, and Snake have targeted manufacturing facilities in particular, stopping output for several days.
- Using logistics access to move beyond conventional boundary fortifications.
Strong OT safety measures that can safeguard critical infrastructure and ensure regulatory compliance are becoming more and more necessary with increasing instances of cyber threats.
Cybersecurity for Legacy Equipment and Brownfield Sites
Many manufacturing facilities, particularly brownfield sites, remain dependent on obsolete equipment and scattered management structures that were never designed for today’s interconnected world for crucial operations. Given their accuracy of operation, these devices pose a severe cybersecurity risk when used in complex manufacturing processes. As they lack integrated security mechanisms such as authorization and password safety, they present a massive attack surface for the cyber criminals.
The legacy programmable logic controllers (PLCs), supervisory systems, and industry control systems (ICS) most commonly use insecure-by-design protocols such as Modbus, DNP3, and Profibus, which lack encryption and authentication and are incongruent with modern network security systems. Even worse, many older systems cannot be patched or updated, making them permanent critical vulnerabilities within the OT network.
Companies must strategically combine risk mitigation and retrofitting to meet these issues. Some of which are listed below:
- Protocol Filtering and Deep Packet Inspection (DPI): These computer tools identify irregularities and prevent unwanted access, especially in outdated systems that lack specific authentication procedures.
- Network Segmentation and Isolation: Separating obsolete technology from other company-owned or internet-connected equipment may assist firms decrease the risk of lateral movement in the case of a breach.
- Secure Gateways and Data Diodes: Interfaces allow limited transfer of information between older and newer structures, avoiding critical equipment from being used as an entry point by cybercriminals.
- Compensating Controls: External security solutions like access control lists, firewalls, or role-based access controls might help safeguard valuable or vulnerable assets, in case of patching not being achievable.
- Asset Inventory and Monitoring: Maintaining a precise record of all legacy systems, combined with real-time monitoring, allows better control over vulnerabilities and a faster response to anomalies.
Building Cyber Resilience in OT Systems
Effective cybersecurity requires vulnerability management and an in-depth knowledge of your OT network structure. A layered security system usually includes:
- Networks that are segmented into operational technology environments and IT zones, to contain hazards.
- Multifactor authorization, that ensures protected remote access to important machinery.
- Systems for detecting anomalies adjusted for predictable OT traffic patterns to minimize false positives.
- Anomaly detection systems that investigate traffic over industrial networks.
- Updating and patching of intelligent and IIoT devices frequently.
- Integrated National Institute of Standards and Technology’s risk assessment and compliance criteria.
Periodic surveillance solutions that investigate data from several industrial operations may quickly identify and pinpoint problems before they affect supply or physical safety.
Bridging IT and OT: Creating Unified Security Architectures
A key characteristic of intelligent production is the combination of information technology (IT) with operational technology (OT). While this enhances data-driven decision-making and operational efficiency, it simultaneously introduces security vulnerabilities stemming from differences in legacy system protocols and procedures.
IT systems promote credibility, anonymity, and accessibility, whereas operational technologies focus on operational uptime, physical security, and system dependability. Connecting these domains necessitates a single security architecture that allows for shared awareness, uniform access rules, and instantaneous threat mitigation across both environments.
To accomplish this, manufacturers should use combined surveillance tools that correlate data from IT and OT networks, identity and access management (IAM) frameworks for controlling user access rights throughout systems, and centralized governance models that define responsibilities and rules for both teams. To optimize innovation, productivity, and security, IT security professionals and OT engineers must collaborate to protect both physical and digital assets.
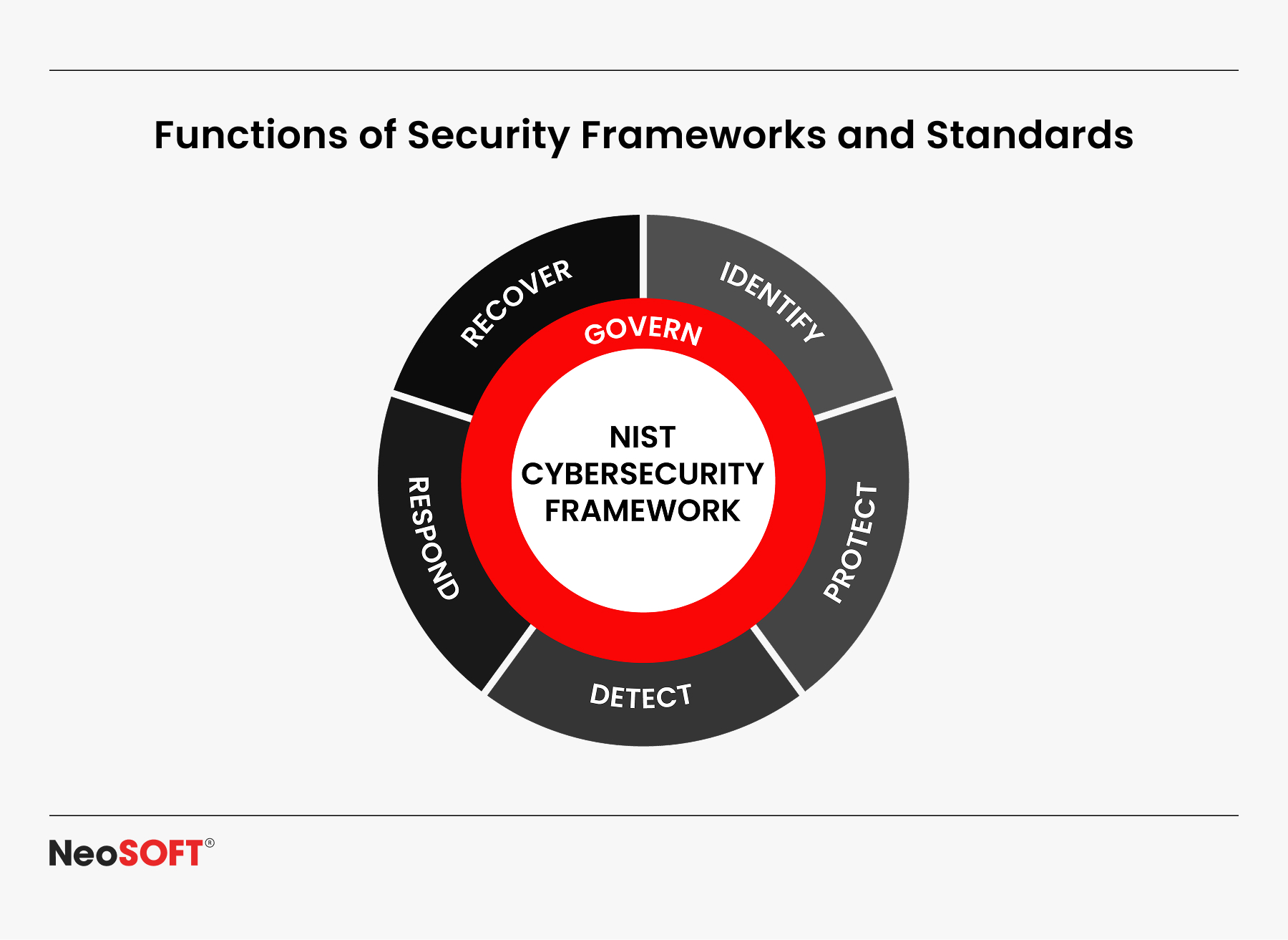
Functions of Security Frameworks and Standards
Adopting recognized frameworks, such as the Cybersecurity Framework developed by NIST (CSF), provides an organized strategy in managing cyber threats through five main operations: identify, safeguard, locate, respond, and recover, allowing manufacturers to create a flexible & scalable security posture that is tailored to their specific risk profile.
ISA/IEC 62443 additionally offers suggestions for securing business operations and automation technologies (IACS). It supports security-by-design methods at the part, software, and network layers, defining roles among asset stockholders, integrators, and suppliers to ensure end-to-end security protection.
These requirements are essential to companies with defined infrastructure, where downtime can result in serious consequences. Standardized security terminology helps manufacturing companies to plan professional events, interact efficiently with suppliers, and maintain standards.
Compliance and Regulatory Demands in Industrial Cybersecurity
Compliance with regional and international laws such as the GDPR, CMMC, NIS2, is an important parameter for the producers working with vital infrastructure. Along with increasing regulatory compliance it also works towards enhancing the dependability of the OT, industrial automation, and controls.
Regulatory frameworks like the Cybersecurity Framework created by NIST promote methodical approaches for threat detection, exposing executives, and data protection. Adhering to them decreases the likelihood of cyber risks, minimizes opportunities for attack in OT networks, and strengthens your capacity to safeguard gadgets that are connected, networked control systems, and important intellectual property.
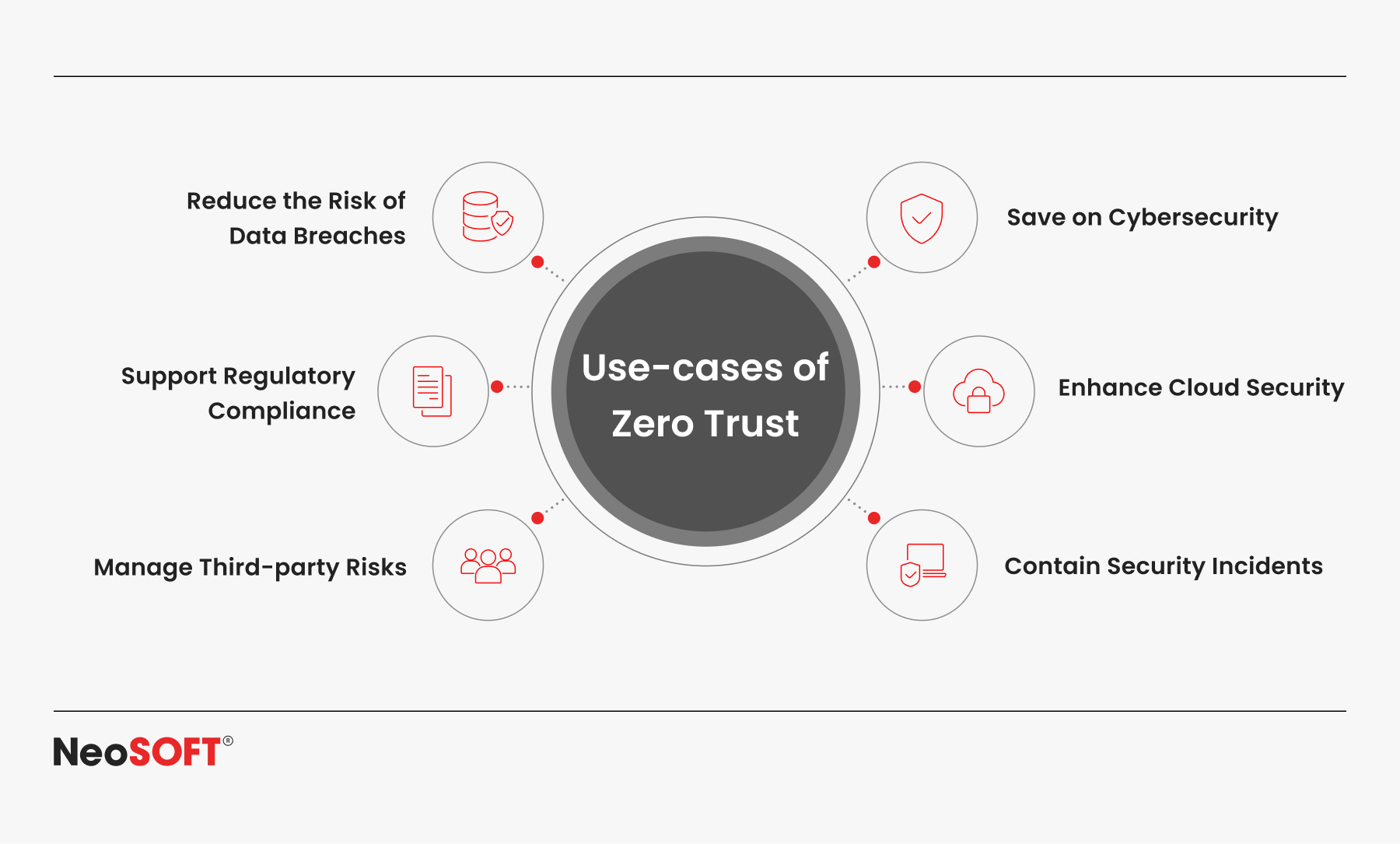
Role of “Zero Trust” in Manufacturing Environment
Traditional defensive measures are falling short as the production sector increasingly relies on Internet of Things (IoT) and remote access solutions. The Zero Trust method, which constantly monitors every user, device, and information flow, offers a more reliable network for modern industrial situations.
Organizations that deploy Zero Trust architecture across OT systems can prevent cyber criminals’ lateral movement, confine threats within industrial networks, and safeguard vital assets such as PLCs and IIoT devices.
Zero Trust principles can significantly reduce lateral movement in OT networks, but applying them fully in legacy ICS setups may require adjustments to meet vendor-specific limits and real-time control requirements.
Achieving zero trust in industrial control systems involves continuous information transparency throughout OT systems and the integration of distributed control systems and IIoT devices. Security teams must make use of cutting-edge tools to analyze data transfers within networks.
Zero Trust is a responsive and continuous strategy that, when combined with the fundamentals provided by the NIST Cybersecurity Framework, ensures uniform regulations across IT and OT environments. Furthermore, it reduces the threat surface for cybercriminals, consequently enhancing operational resilience.
Countering Downtime and Data Breaches in the Manufacturing Sector
Protecting the manufacturing process from data breaches and cyber attacks requires more than firewalls. Companies must take a comprehensive view of security, incorporating:
- Endpoint security for IoT devices
- AI-assisted threat intelligence
- Role-based access controls for factory floor systems
- Isolation zones for testing and validating new technologies
- Constant education for security teams and operators
Mitigation of cyber risks improves safety and operational efficiency, along with protecting production, both of which are important for modern industrial success.
Incident Response Planning and Cyber Resilience
In an era of advanced cyber attacks on manufacturing businesses, incident response preparation is no longer viable. An established response system designed for OT environments should incorporate continuous detection, risk containment, root-cause forensics, and recovery workflows to minimize disturbance to physical processes and industrial operations.
Manufacturing businesses can decrease downtime caused by cyber fraud attacks through carrying out regular cybersecurity mock drills and maintaining forensic readiness, enhancing their production systems’ assurance and dependability.
Securing the Frontlines: Cybersecurity Awareness for Plant Operations Staff
Human error remains an enormous cyber hazard in smart factories, which employ technology but are run by humans. Employee and staff training on optimal security practices, incident reporting, and secure usage of industrial networks helps contribute to the development of a cyber-savvy workspace. This method ensures that your frontline people work as part of your security team, promoting an alert mindset throughout the production process.
As OT and IT systems grow more linked, cross-functional training becomes increasingly crucial in preparing teams to spot cyber dangers that transcend traditional operations and digital systems. Scenario-based training, mock phishing drills, and engaging seminars allow staff to effectively react to practical attack vectors.
Businesses could close the gap across operational technology and data security by encouraging collaboration among security teams and plant staff, resulting in a robust workforce capable of defending industrial operations from growing cyber hazards.
The Future of Industrial Cybersecurity
As industry 4.0 advances, the production sector faces an acceleration in the convergence of advanced technologies and smart gadgets, ranging from industrial robots to automated production lines, broadening the digital attack surface. Greater connectivity boosts operational efficiency, but it additionally introduces new security threats and vulnerabilities to operational technology systems and industrial networks.
To be secure and robust, industrial frameworks must incorporate secure-by-design technologies, enable real-time evaluation, and carry out interoperability standards. Seamless interaction between corporate information technology and cloud platforms is also required to retain visibility and control.
Actively investing in cybersecurity today will ensure that production processes are not only adaptable and intelligent but also capable of withstanding the changing threat landscape, providing physical safety and operational consistency.
Conclusion
Cybersecurity is no longer exclusively an IT issue, it has become a vital part of modernization enabling resilient operations throughout the manufacturing industry. When industrial operations improve and become more connected through IIoT devices, information stored on cloud platforms, and sophisticated platforms, the attack surface grows tremendously. In order to safeguard these settings more than just conventional firewalls are required; security must be applied to all the layers of the OT network.
An innovative cybersecurity plan safeguards not only your information but also your physical operations, intellectual property, and employee security. From securing PLCs and distributed control systems to battling vulnerabilities developed by third-party vendors and remote entry points, manufacturers must take a comprehensive approach that conforms to emerging standards such as the NIST Cybersecurity Framework and NIS2.
Our custom-made OT security solutions, IIoT frameworks, and incident response methods are intended to improve your control systems, empower your teams, and assure business continuity at scale. Contact us at [email protected] to learn more about how these tailor-made solutions may help you create safe, resilient, and future-ready production environments.